This blog post will discuss what is Cross-Site Request Forgery (CSRF) and how to prevent CSRF using synchronizer token pattern and Double submit token pattern.
What is Cross-Site Request Forgery (CSRF)..?
To prevent this kind of attacks developers can user POST requests for any state changing operations like deactivate account.If we use simple GET request no cookie sending or cookie validation happens at server. But with POST requests cookies are sending with the request, so can do user validation before executing the operation. But still an attacker can use java scripts to manipulate the POST request. So as a developer can do user validation before state changing operation like synchronizer token pattern or Double submit token pattern.
Synchronizer token pattern.
The process of synchronizer token pattern is as below.
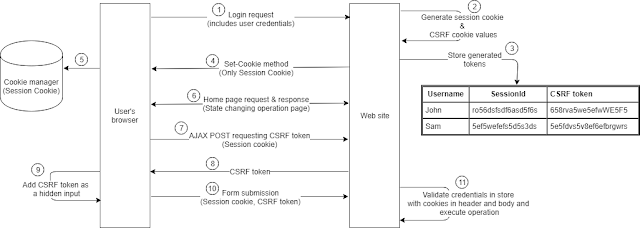
Step 1
Here user submit user credentials to server using a POST request. If we use GET request to send credentials, all the credentials are visible in address bar.
Step 2
Server generate session token value and CSRF token value.
Step 3
Stores generated SESSION cookie value and CSRF token value in server's database.
Step 4
In step 4 Set-Cookie method is coming with the response header. Once executed it generates SESSION cookie. With Http Only flag, java script in the page can not read the cookie with "document.cookie" method. To secure the connection more, can use Secure flag if the connection is HTTPS.
Step 5
In step 5, store cookie came with response in a place known as cookie storage in browser.
Step 6
After step 5 user navigate to the state changing operation page.
Step 7
In this step with document loading an AJAX POST request is going to server to get the CSRF token. This request includes Session cookie in the header. After validating the session cookie server send response including CSRF in step 7.
Step 8
This step shows the response that includes the CSRF value for step 6 (AJAX POST request).
Step 9
In this step Java script add received CSRF value to a hidden input in the form.
Step 10
Step 10 shows the state changing operation. If it is a form submission can send the CSRF token as a hidden input.
Step 11
In here server validated received Session cookie and CSRF with the stored session value and CSRF value and do the state changing operation.
Sample code
Double submit token pattern
The process of double submit cookie pattern is as below.
Here user submit user credentials to server using a POST request. If we use GET request to send credentials, all the credentials are visible in address bar.
Step 2
Server generate session token value and CSRF token value.
Step 3
Stores generated SESSION cookie value in server's database. Not storing the CSRF value in server.
Step 4
In step 4 Set-Cookie method is coming with the response header. Once executed, it generates SESSION cookie and CSRF cookie. With Http Only flag, java script in the page can not read the cookie with "document.cookie" method. CSRF cookie hasn't Http only flag because java scripts in the page need to read the cookie and add it as a hidden input in the form. To secure the connection more, can use Secure flag if the connection is HTTPS.
Step 2
Server generate session token value and CSRF token value.
Step 3
Stores generated SESSION cookie value in server's database. Not storing the CSRF value in server.
Step 4
In step 4 Set-Cookie method is coming with the response header. Once executed, it generates SESSION cookie and CSRF cookie. With Http Only flag, java script in the page can not read the cookie with "document.cookie" method. CSRF cookie hasn't Http only flag because java scripts in the page need to read the cookie and add it as a hidden input in the form. To secure the connection more, can use Secure flag if the connection is HTTPS.
Step 5
In step 5, store cookie came with response in a place known as cookie storage in browser.
Step 6
After step 5 user navigate to the state changing operation page.
Step 7
Received CSRF token is added to a hidden input in the form using a java script.
Step 8
Submit form details with cookies to the server.
Step 9
Server check does the received CSRF in the body match with the CSRF value in the header and validate the session and do the operation.
In step 5, store cookie came with response in a place known as cookie storage in browser.
Step 6
After step 5 user navigate to the state changing operation page.
Step 7
Received CSRF token is added to a hidden input in the form using a java script.
Step 8
Submit form details with cookies to the server.
Step 9
Server check does the received CSRF in the body match with the CSRF value in the header and validate the session and do the operation.







No comments:
Post a Comment